 www.youtube.com
www.youtube.com
cross-posted from: https://lemmy.capebreton.social/post/2509054 > On April 9, 1999 the Domain Controllers for the redmond.corp.microsoft.com Windows NT4-based domain were upgraded to a pre-release version of Windows 2000 Server and thus became the world’s first production Active Directory domain:
 www.youtube.com
www.youtube.com
On April 9, 1999 the Domain Controllers for the redmond.corp.microsoft.com Windows NT4-based domain were upgraded to a pre-release version of Windows 2000 Server and thus became the world’s first production Active Directory domain:
 www.bleepingcomputer.com
www.bleepingcomputer.com
 www.theregister.com
www.theregister.com
 en.wikipedia.org
en.wikipedia.org
 en.wikipedia.org
en.wikipedia.org
 thenewstack.io
thenewstack.io
 www.theregister.com
www.theregister.com
 www.bleepingcomputer.com
www.bleepingcomputer.com
 www.cadosecurity.com
www.cadosecurity.com
 www.nytimes.com
www.nytimes.com
 www.theregister.com
www.theregister.com
 arstechnica.com
arstechnica.com
 arstechnica.com
arstechnica.com
 www.techspot.com
www.techspot.com
 www.nist.gov
www.nist.gov
 techcrunch.com
techcrunch.com
 arstechnica.com
arstechnica.com
 arstechnica.com
arstechnica.com
 videodrome
8 months ago
•
100%
videodrome
8 months ago
•
100%
"Eager to clear his name, Barker said he shared with the police copies of his credit card bills and purchase history at Amazon. But on April 21, the investigator called again to say he was coming to arrest Barker for theft."
 www.fromjason.xyz
www.fromjason.xyz
 www.bleepingcomputer.com
www.bleepingcomputer.com
 www.bleepingcomputer.com
www.bleepingcomputer.com
 www.theregister.com
www.theregister.com
 www.cyber.gc.ca
www.cyber.gc.ca
 www.bleepingcomputer.com
www.bleepingcomputer.com
 www.youtube.com
www.youtube.com
 www.theregister.com
www.theregister.com
 gizmodo.com
gizmodo.com
We’re kicking things off in the new year with a returning guest, Mr. Bil Herd. He was the principal engineer on the Commodore Plus/4, C16/116, C264, C364, and the Commodore 128. Come join us at our usual location, the Alderwood United Church, 44 Delma Dr., Etobicoke ON, M8W 4N6, Canada. The meeting takes place on Thursday, January 11, 2024 at 7:30PM ET. If you’re unable to attend in person, please join us online via the Zoom link below. Thanks for attending! Join Zoom Meeting https://us02web.zoom.us/j/88059151457?pwd=RTEzUWM5bnc4cFpjVjZBYXNEMElEZz09 Meeting ID: 880 5915 1457 Passcode: 274933
 videodrome
9 months ago
•
100%
videodrome
9 months ago
•
100%

 www.bitdefender.com
www.bitdefender.com
In the past, cybercriminals often operated with the motive to "do it for lulz," engaging in malicious activities purely for the sake of amusement or creating chaos. Today, they’re driven by profit, transforming into rational business entities seeking scalable, repeatable processes for a steady income. This change in motivation has made predicting their behavior somewhat easier, as their actions are now grounded in strategic objectives rather than unpredictable whims. In 2024, we expect the ransomware threat will continue taking an opportunistic turn—a trend that we first highlighted in 2022, gained momentum throughout 2023 (marked by multiple advisories, culminating in the ongoing CitrixBleed exploitation), and is projected to reach maturity this year.
Every so often someone needs to create a more or less permanent internal identifier in their system every person's account. Some of the time they look at how authentication systems like OIDC return email addresses among other data and decide that since pretty much everyone is giving them an email address, they'll use the email address as the account's permanent internal identification. *As the famous saying goes, now you have two problems.*
 videodrome
11 months ago
•
100%
videodrome
11 months ago
•
100%
Yes, but just added to the haveibeenpwnd db
 videodrome
11 months ago
•
100%
videodrome
11 months ago
•
100%
Archive link -> https://archive.ph/q9gJJ
 videodrome
11 months ago
•
100%
videodrome
11 months ago
•
100%
drama
 videodrome
11 months ago
•
100%
videodrome
11 months ago
•
100%
Great podcast! 👍
 videodrome
11 months ago
•
100%
videodrome
11 months ago
•
100%
sorry… fucking hell i’m old.
haha, I too suffer from the same affliction. 👴
 videodrome
12 months ago
•
100%
videodrome
12 months ago
•
100%
FROM THE ARTICLE:
Exploitation and Impact
In GuardLapse, there are two main exploitation routes:
1. Cracking the Password Hash
Malicious Malory can set up a rogue SMB server. Instead of working as expected, this server accepts authentication requests and grabs the password hash.
If she cracks the password hash successfully, she gains access to whatever the WatchGuard AD account can access.
Even with ZERO privileges assigned to the WatchGuard AD account, authenticated access to the domain in AD environments exposes many attack avenues - Kerberoasting, user enumeration for password spraying, BloodHound recon, and more.
2. SMB Relaying
If other domain PCs don't require SMB signing, she can directly relay the authentication requests to access targeted hosts, eliminating the need to crack the password hash! (This depends on the AD account having admin privileges on targeted hosts).
To show the impact, in my recent engagement, we transitioned from an unauthenticated device on the network to Domain Admin using this issue. We relayed WatchGuard authentication requests to get an initial foothold on several devices. We then exploited other vulnerabilities to secure Domain Admin privileges.
WatchGuard's Response
When I contacted WatchGuard about the behaviour I observed, they responded promptly and helpfully.
They pointed me to the documentation about WatchGuard's Clientless AD SSO methods, which they thought explained what I saw. When I asked about their plans to retire or rework this feature, WatchGuard said they might retire AD Mode but would keep the Event Log Monitor.
They also said they were exploring options to enhance the visibility of security risks associated with Clientless SSO based on my report.
Action
If you use a WatchGuard firewall and rely on clientless SSO, my current, unvalidated recommendation is:
Switch off AD mode and rely on the SSO Client. Remove the Event Log Monitor if you've installed it. NOTE: I haven't validated this fix because I don't own a WatchGuard firewall. If you want to collaborate to validate this fix, please get in touch!
I've also asked WatchGuard for their remediation advice given their customers' current risk. Once they reply, I'll update this post with their guidance.
 videodrome
12 months ago
•
100%
videodrome
12 months ago
•
100%
 videodrome
12 months ago
•
100%
videodrome
12 months ago
•
100%
He's very, very wrong and there are some good answers above as to the why.
Did he give you an example application where he practices this password-free lifestyle?
 videodrome
12 months ago
•
100%
videodrome
12 months ago
•
100%
What are your opinions about this?
I just don't understand his statement , can you elaborate more?
 videodrome
12 months ago
•
100%
videodrome
12 months ago
•
100%
 videodrome
12 months ago
•
100%
videodrome
12 months ago
•
100%
Glad to see another Lemmy.CapeBreton community :) , !computerhistory@lemmy.capebreton.social
 videodrome
1 year ago
•
100%
videodrome
1 year ago
•
100%

 videodrome
1 year ago
•
100%
videodrome
1 year ago
•
100%
One of my favs
 videodrome
1 year ago
•
100%
videodrome
1 year ago
•
100%
 videodrome
1 year ago
•
100%
videodrome
1 year ago
•
100%
I think this is a problem in tech/it careers in general
 videodrome
1 year ago
•
100%
videodrome
1 year ago
•
100%
They are next
 videodrome
1 year ago
•
100%
videodrome
1 year ago
•
100%
Fixed it ... The image url appears to have overwritten the actual URL when I posted
https://thehistoryoftheweb.com/postscript/aol-pretends-to-be-the-internet/
 videodrome
1 year ago
•
100%
videodrome
1 year ago
•
100%
If it's not related to the topic of the community, report and I will remove.
I'll be doing a cleanup of some of the feeds to remove some of the lower content sites over the coming days
 videodrome
1 year ago
•
100%
videodrome
1 year ago
•
100%
I too enjoyed this movie
 videodrome
1 year ago
•
100%
videodrome
1 year ago
•
100%
I just started watching this series.
It is very, very good 👍
 videodrome
1 year ago
•
100%
videodrome
1 year ago
•
100%
One of my fav communities right now, hobbydrama is some of the best drama
 videodrome
1 year ago
•
100%
videodrome
1 year ago
•
100%
https://blog.phylum.io/rust-malware-staged-on-crates-io/ is a better article with details.
ty for article recommendation ... much better!
 videodrome
1 year ago
•
100%
videodrome
1 year ago
•
100%

 videodrome
1 year ago
•
100%
videodrome
1 year ago
•
100%
Amass
The OWASP Amass project performs network mapping of attack surfaces and external asset discovery using open-source information gathering and active reconnaissance techniques.
Osmedeus
Osmedeus is a workflow engine for offensive security that allows you to build and run a reconnaissance system on a wide range of targets, including domains, URLs, CIDRs, and GitHub repositories. It was designed to establish a strong foundation and can adapt and function automatically to perform reconnaissance tasks.
PhoneInfoga
PhoneInfoga is an advanced tool to scan international phone numbers. It allows you to gather basic information such as country, area, carrier, and line type, then use various techniques to find the VoIP provider or identify the owner. It works with a collection of scanners that must be configured for the tool to be effective.
Sherlock
Sherlock allows you to search social media accounts by username across social networks.
Shodan
Shodan is a search engine for Internet-connected devices. Discover how internet intelligence can help you make better decisions. The entire Shodan platform (crawling, IP lookups, searching, and data streaming) is available to developers. Use their API to understand whether users connect from a VPN, whether the website you’re visiting has been compromised, and more.
Social Analyzer
Social Analyzer is an API, CLI, and web app for analyzing and finding a person’s profile across social media and websites. It includes different analysis and detection modules; you can choose which modules to use during the investigation process. The analysis and public extracted information from this OSINT tool could help investigate profiles related to suspicious or malicious activities such as cyberbullying, cyber grooming, cyberstalking, and spreading misinformation.
SpiderFoot
SpiderFoot is an OSINT automation tool. It integrates with just about every data source available and utilizes a range of methods for data analysis, making that data easy to navigate. SpiderFoot has an embedded web-server for providing a clean and intuitive web-based interface but can also be used completely via the command-line.
theHarvester
theHarvester is a simple to use, yet powerful tool designed to be used during the reconnaissance stage of a red team assessment or penetration test. It performs OSINT gathering to help determine a domain’s external threat landscape. The tool gathers names, emails, IPs, subdomains, and URLs by using multiple public resources.
 videodrome
1 year ago
•
100%
videodrome
1 year ago
•
100%
The method "tricks the victim into thinking their device's Airplane Mode works when in reality the attacker (following successful device exploit) has planted an artificial Airplane Mode which edits the UI to display Airplane Mode icon and cuts internet connection to all apps except the attacker application," Jamf Threat Labs researchers Hu Ke and Nir Avraham said in a report shared with The Hacker News.
The approach devised by Jamf, in a nutshell, provides an illusion to the user that the Airplane Mode is on while allowing a malicious actor to stealthily maintain a cellular network connection for a rogue application.
 videodrome
1 year ago
•
100%
videodrome
1 year ago
•
100%
Great story!
Love reading all the nostalgia these historical tidbits inevitably bring up
 videodrome
1 year ago
•
100%
videodrome
1 year ago
•
100%
That is an excellent interview ... Thanks for sharing.
That certainly adds to the whole problem with payouts.
 videodrome
1 year ago
•
100%
videodrome
1 year ago
•
100%
I sadly missed those days :(
 videodrome
1 year ago
•
100%
videodrome
1 year ago
•
100%
Good point about the cyber-insurance aspect of things perpetuating the problem.
I don't have hard data but I believe this will be a thing of the past soon enough. With ransomware being so common an issue now & the requirements to obtain said insurance getting harder to meet, I could see that not being a viable or cost-effective solution to restoring service.
 videodrome
1 year ago
•
100%
videodrome
1 year ago
•
100%
Never pay ... I'm pretty sure there is an aesops fable about a farmer and a snake that gives you the best advice on this issue.
 videodrome
1 year ago
•
100%
videodrome
1 year ago
•
100%
That tracks with my experience as that time period covers the start of my career.
That being said, it goes back even farther.
 videodrome
1 year ago
•
100%
videodrome
1 year ago
•
100%
IT had the stupid grind culture well before it became a meme.
 videodrome
1 year ago
•
100%
videodrome
1 year ago
•
100%
Active flaws in the PowerShell Gallery could be weaponized by threat actors to pull off supply chain attacks against the registry's users.
"These flaws make typosquatting attacks inevitable in this registry, while also making it extremely difficult for users to identify the true owner of a package," Aqua security researchers Mor Weinberger, Yakir Kadkoda, and Ilay Goldman said in a report shared with The Hacker News.
Maintained by Microsoft, PowerShell Gallery is a central repository for sharing and acquiring PowerShell code, including PowerShell modules, scripts, and Desired State Configuration (DSC) resources. The registry boasts 11,829 unique packages and 244,615 packages in total.
The issues identified by the cloud security firm have to do with the service's lax policy surrounding package names, lacking protections against typosquatting attacks, as a result enabling attackers to upload malicious PowerShell modules that appear genuine to unsuspecting users.
A second flaw pertains to the ability of a bad actor to spoof the metadata of a module -- including Author(s), Copyright, and Description fields -- to make it appear more legitimate, thereby deceiving unwitting users into installing them.
"The only way for users to determine the real author/owner is to open the 'Package Details' tab," the researchers said.
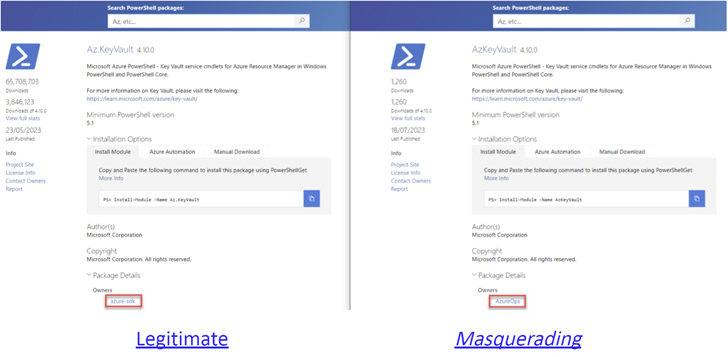
"However, this will only lead them to the profile of the fake author, as the attacker can freely choose any name when creating a user in the PowerShell Gallery. Therefore, determining the actual author of a PowerShell module in the PowerShell Gallery poses a challenging task."
Also discovered is a third flaw that could be abused by attackers to enumerate all package names and versions, including those that are unlisted and meant to be hidden from public view.
This can be accomplished by utilizing the PowerShell API "https://www.powershellgallery.com/api/v2/Packages?$skip=number," enabling an attacker to gain unrestricted access to the complete PowerShell package database, including associated versions.
"This uncontrolled access provides malicious actors with the ability to search for potential sensitive information within unlisted packages. Consequently, any unlisted package that contains confidential data, becomes highly susceptible to compromise," the researchers explained.
Aqua said it reported the shortcomings to Microsoft in September 2022, following which the Windows maker is said to have put in place reactive fixes as of March 7, 2023. The problems, however, remain reproducible.
"As we increasingly depend on open-source projects and registries, the security risks associated with them become more prominent," the researchers concluded.
"The responsibility for securing users primarily lies with the platform. It's essential that PowerShell Gallery, and similar platforms, take necessary steps to enhance their security measures."
 videodrome
1 year ago
•
100%
videodrome
1 year ago
•
100%
Considering the global turbulence from destabilizing events such as physical conflicts, freak weather and pandemics, financial wealth has never been more critical for a nation and its citizens so that daily life can continue. Money is needed for daily necessities such as food, medication, appropriate clothing and fuel. When faced with unexpected events such as retrenchment and newly detected health issues, citizens would also have to tap on the monetary buffer that should have been built up during less challenging times. Considering the current state of international affairs and employment prospects, one potential way to disrupt a nation’s peace and stability could be stealing their citizens’ monetary savings via financial scams and fraud.
Unlike conventional cyber-attacks such as phishing, where adversaries target to harvest credentials to gain access to accounts, digital scams aim to bypass the harvesting of credentials but instead attempt to convince the victim to authenticate and part with their assets directly. A multitude of factors could cause this change. For example, end users have gotten savvier about phishing attacks and stopped interacting with such messages that try to masquerade as a well-known entity (e.g. shipping companies/social media sites). Applications could also have implemented additional security controls such as two-factor authentication (2FA), preventing adversaries from directly using credentials to authenticate with the target application. The main issue is that adversaries are likely to employ some means to wire away a victim’s hard-earned money and keep on doing so should these tactics be successful.
There have been a few notable case studies where adversaries do not simply send phishing messages but also pray on victims’ psychological weaknesses and informational blind spots. I was made aware of such an incident that was reported to me privately about 60 hours ago, where an adversary attempted to masquerade as a charitable organization. In this particular incident, the charitable organization had a legitimate and actual event that had been scheduled. There were also corresponding marketing materials with Quick Response (QR) codes embedded in the posters. Participants could register for the event by donating any amount via the QR code (using the local Singapore QR code payment system) and sending the receipt to a number shown on the poster. Most event details were correct; even the e-mail address shown was legitimate. However, upon closer inspection and after some analysis, it was determined that the actual event had already been held, and the QR code used for payments pointed to an account not affiliated with the charitable organization. Meanwhile, the “semi-fictitious” event had been circulated via popular messaging platforms such as Telegram. It is unclear if anyone made any payments to the monetary account that the scammer set up, but the original message had been removed.
Another recent attack that led to victims losing their money was the installation of third-party mobile applications that were not downloaded from legitimate and trusted mobile application stores. For example, in this unfortunate incident, the victim was left with only about ~US$2.95 (S$4) in the bank account after unknowingly installing a purported update to a mobile application [1]. The Federal Bureau of Investigation (FBI) also issued a Public Service Announcement (PSA) about cyber criminals targeting victims through mobile beta-testing applications, which could lead to monetary losses [2]. This was also highlighted in the Wednesday, August 16th 2023, SANS Internet Storm Center Stormcast [3].
Security controls can only do so much in preventing such unfortunate incidents. Due to financial challenges, not everyone can afford the latest phones, which may come promised with security support. Depending on the vendors, certain phones may not even receive timely security patches, and adversaries could tap into those vulnerabilities to perpetuate their digital scams. It could also be user-induced due to the removal of security controls designed to secure phones (e.g. rooting (for Android) or jail-breaking (for iOS)). There is room for research on possible ways to disrupt and deny adversaries who perpetuate such digital scams while factoring in current technical limitations and scenarios. However, without any technological implementation, awareness of these digital scams is paramount as a first step towards foiling such attacks. No doubt such attack techniques may seem trivial to cybersecurity professionals since we are aware of such dangers, other individuals may not fully understand the potential dangers of such digital scams. It would be worthwhile to consider having conversations and greater awareness about these digital scams in your organization and among friends and families.
References:
- https://www.asiaone.com/singapore/only-4-left-single-mum-loses-28k-after-phone-gets-hacked-realises-she-has-2-chromes
- https://www.ic3.gov/Media/Y2023/PSA230814
- https://isc.sans.edu/podcastdetail.html?podcastid=8618
Yee Ching Tok, Ph.D., ISC Handler
 videodrome
1 year ago
•
100%
videodrome
1 year ago
•
100%
It's very effective at building the habit and practice of running. I am glad I did it and would love to help others on their "journey"
 videodrome
1 year ago
•
100%
videodrome
1 year ago
•
100%
How could you possibly prove that all copies have been deleted?
That's always the best part of these articles-- we believe the extortionists will not try to further extort us based on their word (or a screenshot of an empty folder)
 videodrome
1 year ago
•
100%
videodrome
1 year ago
•
100%
We have cozy bear to hold us over till then